How Much do You Know About AppSec?
The Ultimate AppSec Trivia Challenge is a fun and educational game that tests your application security knowledge. The game consists of questions ranging from easy to hard, all related to application security.

What position is Injection on OWASP TOP 10 2021
Level: Easy
Injection vulnerabilities have been in the OWASP Top 10 since its creation.
What does OWASP stand for?
Level: Easy
In 2023 OWASP changed its name from Open Web Application Security Project, to make it more inclusive to the different aspects of application security.
What will appear on the page?
Level: Easy
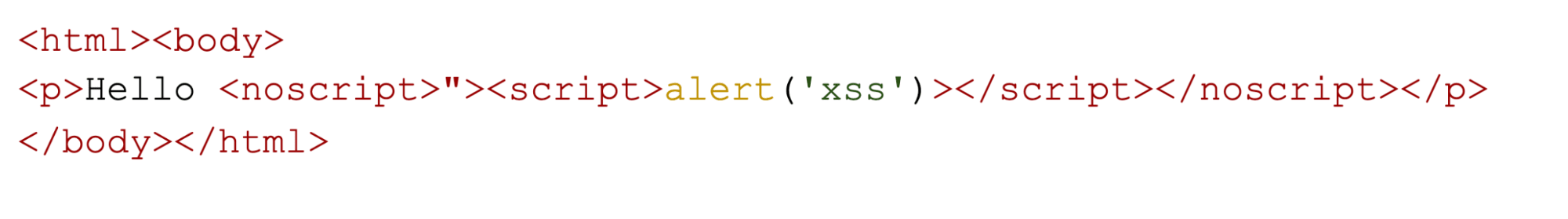
The noscript tag prevents the script tag from being interpreted.
What does CIA in the CIA triad stand for?
What is the newer name for Insecure Direct Object Reference vulnerabilities?
What does CSRF stand for?
If an unauthenticated user can access a private URL from a privileged user, what is the associated OWASP Top 10 risk?
If your application logs can be tampered with, which OWASP Top 10 risk is applicable?
What is the other name for Clickjacking?
What risk is in the last position of the OWASP Top 10?
What is the vulnerability?

You are using Windows XP. Which OWASP Top 10 risk applies here?
Windows XP support ended in 2014.
You see this in a browser. What OWASP Top 10 risk does it refer to?

In which year was the OWASP Top 10 published for the first time?
The usage of “questions and answers” in a credential recovery workflow can be associated with which OWASP Top 10 risk?
Various industry guidelines and standards, such as OWASP ASVS, OWASP Top 10, and NIST 800-63b consider this an insecure design.
RSA stands for?
These are the first names of the three creators of the widely used RSA cryptographic algorithm
Name the 3 types of XSS
A software distribution system that doesn’t provide integrity assurances is violating which OWASP Top 10 risk?
A padding oracle vulnerability refers to which risk of the OWASP Top 10?
Which cookie attribute prevents CSRF?
What is the authentication algorithm used in the following cipher suite:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
RSA: The 1st part is the key exchange algorithm, 2nd, the authentication, 3rd encryption, and 4th is the MAC.
SSDLC Stands for?
The HTTP 429 response code means?
Will the alert execute?
HTTP/1.1 200 OK
date: Thu, 06 Apr 2023 21:53:38 GMT
strict-transport-security: max-age=31536000; includeSubDomains
vary: origin,accept-encoding
content-type: application/json; charset=utf-8
x-content-type-options: nosniff
x-frame-options: DENY
x-xss-protection: 1; mode=block
<html><body><h1>Hello <script>alert(13)</script></h1></body></html>
No, because the content-type is application/json, which will not be rendered by the browser.
CVSS stands for?
What is the PR in CVSS?
Privileges Required: It can have three values: None, Low or High
Name the attack.
GET /?error=foobar%0d%0aSet-Cookie:+sessionid=abcdef
host: example.com
HTTP/1.1 301 Moved Permanently
Location: /index?error=foobar
Set-Cookie: sessionid=abcdef
What vulnerability is this payload used for?
${T(java.lang.System).getenv()}
What does SBOM stands for?
Software Bill of Materials. SBOM’s are an inventory of all the components of a given software.
sqlmap -D parameter is used for:
What is AWS metadata IP:
How old can cookies be before the SameSite Lax-Allowing-Unsafe enforces the Lax rules?
Cookies newer than 2 minutes, can be sent on requests cross-domain, just like in a SameSite=None scenario. After 2 minutes, the Lax configuration is applied.
What is the name of the first XSS worm:
Will the alert execute?
GET /?name=<script>alert(13)<%2Fscript> HTTP/1.1
host: example.com
HTTP/1.1 200 OK
date: Thu, 06 Apr 2023 21:53:38 GMT
content-security-policy: default-src js.example.com;
x-content-type-options: nosniff
x-frame-options: DENY
x-xss-protection: 1; mode=block
referer: example.com/?name=<script>alert(13)<%2Fscript>
<html><body><h1>Hello <script>alert(13)</script></h1></body></html>
Answer:
No, because the Content Security Policy only allows for JavaScript from js.example.com
In a SQL injection payload, what can you use instead of whitespaces?
For instance, 0/**/or/**/1 is the same as 0 or 1.
What is the CVSS rating of:
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H?
9.0 or Critical. It is not a 10 because the Attack Complexity (AC) is High (H) and not Low (L)
What is the E in CVSS 3 Temporal Score?
The “goto fail;” vulnerability affected which functionality?
List the OWASP Top 10 in order, from A01 to A10.
A):
A01 Broken Access Control
A02 Cryptographic Failures
A03 Injection
A04 Insecure Design
A05 Security Misconfiguration
A06 Vulnerable and Outdated Components
A07 Identification and Authentication Failures
A08 Software and Data Integrity Failures
A09 Security Logging and Monitoring Failures
A10 Server-Side Request Forgery (SSRF)
B):
A01 Broken Access Control
A02 Cryptographic Failures
A03 Insecure Design
A04 Injection
A05 Security Misconfiguration
A06 Vulnerable and Outdated Components
A07 Software and Data Integrity Failures
A08 Identification and Authentication Failures
A09 Security Logging and Monitoring Failures
A10 Server-Side Request Forgery (SSRF)
Name one of the two most common JWT signing algorithms
You got {number correct}/{number of questions} correct answers
Well, You are a Newbie!
It seems you are just starting out. Your effort is commendable though.

You got {number correct}/{number of questions} correct answers
Awesome! You are experienced!
Well done! You have an understanding of Appsec fundamentals.

You got {number correct}/{number of questions} correct answers
Whoa! You are an Expert!
That's some great score!
You have an excellent hold on all the nuances of Appsec. People learn from you, but don't forget there is always room for improvement. Keep on learning and inspiring others. The digital world needs you!